Biometrics
Some consider biometrics as intrusive and as a violation of privacy. While you read, pay attention to how biometric systems authenticate and to the three main threats against biometric systems. What are these three threats and what are the cryptographic and non-cryptographic countermeasures?
3. Main Threats against Privacy-Preserving Biometric Authentication Systems
3.3. User Traceability and Distinguishability
Generally speaking, attacks against the user's privacy (in the sense of traceability and distinguishability) do not aim at gathering information about the user's biometric credential in itself, but rather at profiling and identifying the target user among
all the users of one or more biometric systems.
The main attack strategy to trace users in privacy-preserving BAS is the following. The attacker gets access to different databases (possibly in use by different biometric authentication systems) and successfully traces a user's authentication attempts, by checking which record of the database is queried (as match for the authentication). Note that the above approach does not require the attacker to know the user's credential, as long as the databases store the biometric credentials in the same way (i.e., using the same encryption mechanism and the same secret key). Luckily, in real life, this is a very strong assumption which happens only seldom.
In simple words, user distinguishability can be considered as user tracing over different authentication attempts in the same or different authentication systems. That is, the attacker can recognise the target user among the other users present in the biometric authentication system. This attack is always successful if the attacker learns the mapping from the set of identities to the set of (encrypted) templates. In other words, an attacker can distinguish users if he learns that to a certain identity corresponds
a certain (possibly encrypted) template
corresponds
a certain (possibly encrypted) template  . A
solution would be to keep the mapping
. A
solution would be to keep the mapping 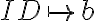 secret or to use a (secure) pseudorandom mapping. Another possibility is to ensure that the communication channels between the entities involved in the BAS are secure or that the information transmitted is encrypted using chosen
plaintext attacks- (CPA-) secure systems.
secret or to use a (secure) pseudorandom mapping. Another possibility is to ensure that the communication channels between the entities involved in the BAS are secure or that the information transmitted is encrypted using chosen
plaintext attacks- (CPA-) secure systems.
The main attack strategy to trace users in privacy-preserving BAS is the following. The attacker gets access to different databases (possibly in use by different biometric authentication systems) and successfully traces a user's authentication attempts, by checking which record of the database is queried (as match for the authentication). Note that the above approach does not require the attacker to know the user's credential, as long as the databases store the biometric credentials in the same way (i.e., using the same encryption mechanism and the same secret key). Luckily, in real life, this is a very strong assumption which happens only seldom.
In simple words, user distinguishability can be considered as user tracing over different authentication attempts in the same or different authentication systems. That is, the attacker can recognise the target user among the other users present in the biometric authentication system. This attack is always successful if the attacker learns the mapping from the set of identities to the set of (encrypted) templates. In other words, an attacker can distinguish users if he learns that to a certain identity